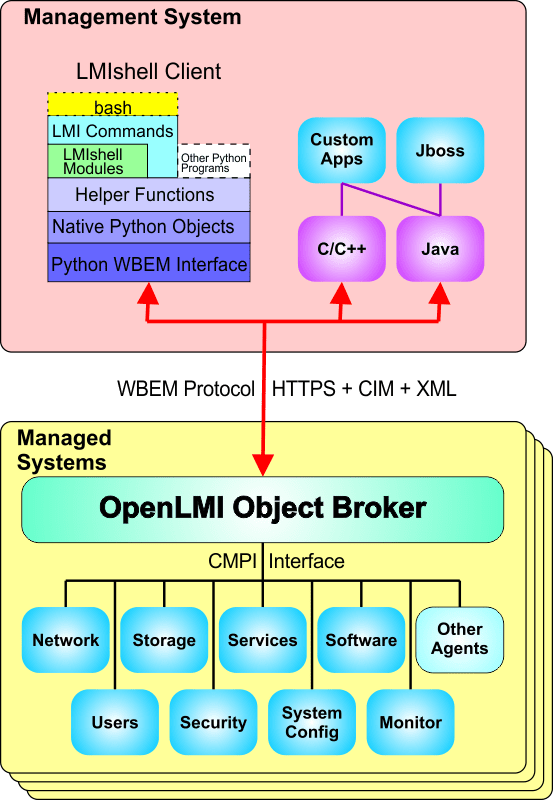
Exciting news – a major update to the OpenLMI CLI is available! The new CLI adds support for configuring networks, reworks the storage commands, provides a command hierarchy in the interactive shell, and includes internal improvements.
Let’s start with the new LMI command structure. Use lmi help to see the new interface:
lmi> help
Static commands
===============
EOF exit help
Application commands (type help <topic>):
=========================================
file group hwinfo net power service storage sw system user
Built-in commands (type :help):
===============================
:.. :cd :pwd :help
One obvious change is that all of the storage related commands have been combined into a single top level storage command – you now begin all storage operations with the keyword storage. At the same time, a new shell option supports command hierarchy. If you are going to be entering a series of storage commands, you can “move down” to that level by using the “:cd” command. You move back up to a higher level in the command hierarchy by using the “:..” command.
lmi> :cd storage
>storage>
You can now enter storage commands directly – for example, list available storage devices:
lmi> :cd storage
>storage>
>storage> list
Name Size Format
/dev/sda 320072933376 MS-DOS partition table
/dev/mapper/luks-fe998f70-9da9-4049-88db-47d9db936b82 319545147392 physical volume (LVM)
/dev/sda1 524288000 ext4
/dev/sda2 319547244544 Encrypted (LUKS)
/dev/mapper/vg_rd230-lv_home 259879075840 ext4
/dev/mapper/vg_rd230-lv_root 53687091200 ext4
/dev/mapper/vg_rd230-lv_swap 5972688896 swap
>storage>
In a change from the previous version, the storage list command now includes only the friendly device name. This means you no longer need a 200 column terminal window to get all the information on one like.
Like the previous version of the storage command, you can get detailed information on each device. Entering storage show will list details for all storage devices. Entering storage show devicename will give detailed information for just that device. For example, to get details on device sda:
>storage> show sda
Name Value
/dev/disk/by-id/ata-HITACHI_HTS725032A7E630_TF1401Y1G0EZAF:
Name Value
Type Generic block device
DeviceID /dev/disk/by-id/ata-HITACHI_HTS725032A7E630_TF1401Y1G0EZAF
Name /dev/sda
ElementName sda
Total Size 320072933376
Block Size 512
Data Type Partition Table
Partition Table Type MS-DOS
Partition Table Size (in blocks) 1
Largest Free Space 0
Partitions /dev/sda1 /dev/sda2
>storage>
Another significant improvement is support for thin provisioning through the thinpool and thinlv commands:
>storage> help thinpool
Thin Pool management.
Usage:
thinpool list
thinpool create <name> <vg> <size>
thinpool delete <tp> …
thinpool show [ <tp> …]
Commands:
list List all thin pools on the system.
create Create Thin Pool with given name and size from a Volume Group.
delete Delete given Thin Pools.
show Show detailed information about given Thin Pools. If no
Thin Pools are provided, all of them are displayed.
Options:
vg Name of the volume group, with or without `/dev/` prefix.
tp Name of the thin pool, with or without `/dev/` prefix.
size Requested extent size of the new volume group, by default in
bytes. ‘T’, ‘G’, ‘M’ or ‘K’ suffix can be used to specify
other units (TiB, GiB, MiB and KiB) – ‘1K’ specifies 1 KiB
(=1024 bytes).
The suffix is case insensitive, i.e. 1g = 1G = 1073741824 bytes.
>storage> help thinlv
Thin Logical Volume management.
Usage:
thinlv list [ <tp> …]
thinlv create <tp> <name> <size>
thinlv delete <tlv> …
thinlv show [ <tlv> …]
Commands:
list List available thin logical volumes on given thin pools.
If no thin pools are provided, all thin logical volumes are
listed.
create Create a thin logical volume on given thin pool.
delete Delete given thin logical volume.
show Show detailed information about given Thin Logical Volumes. If no
Thin Logical Volumes are provided, all of them are displayed.
Options:
tp Name of the thin pool, with or without `/dev/` prefix.
size Size of the new logical volume, by default in bytes.
‘T’, ‘G’, ‘M’ or ‘K’ suffix can be used to specify other
units (TiB, GiB, MiB and KiB) – ‘1K’ specifies 1 KiB
(= 1024 bytes).
The suffix is case insensitive, i.e. 1g = 1G = 1073741824
bytes.
>storage>
We will take a look at other parts of the OpenLMI CLI commands in future articles.